Particular because of Vlad Zamfir for a lot of the considering behind multi-chain cryptoeconomic paradigms
First off, a historical past lesson. In October 2013, once I was visiting Israel as a part of my journey across the Bitcoin world, I got here to know the core groups behind the coloured cash and Mastercoin tasks. As soon as I correctly understood Mastercoin and its potential, I used to be instantly drawn in by the sheer energy of the protocol; nonetheless, I disliked the truth that the protocol was designed as a disparate ensemble of “options”, offering a subtantial quantity of performance for individuals to make use of, however providing no freedom to flee out of that field. In search of to enhance Mastercoin’s potential, I got here up with a draft proposal for one thing known as “final scripting” – a general-purpose stack-based programming language that Mastercoin might embrace to permit two events to make a contract on an arbitrary mathematical formulation. The scheme would generalize financial savings wallets, contracts for distinction, many sorts of playing, amongst different options. It was nonetheless fairly restricted, permitting solely three levels (open, fill, resolve) and no inside reminiscence and being restricted to 2 events per contract, but it surely was the primary true seed of the Ethereum thought.
I submitted the proposal to the Mastercoin crew. They have been impressed, however elected to not undertake it too shortly out of a want to be gradual and conservative; a philosophy which the challenge retains to to at the present time and which David Johnston talked about on the latest Tel Aviv convention as Mastercoin’s major differentiating function. Thus, I made a decision to exit alone and easily construct the factor myself. Over the following three weeks I created the unique Ethereum whitepaper (sadly now gone, however a nonetheless very early model exists right here). The fundamental constructing blocks have been all there, besides the progamming language was register-based as a substitute of stack-based, and, as a result of I used to be/am not expert sufficient in p2p networking to construct an unbiased blockchain consumer from scratch, it was to be constructed as a meta-protocol on high of Primecoin – not Bitcoin, as a result of I needed to fulfill the issues of Bitcoin builders who have been indignant at meta-protocols bloating the blockchain with additional information.
As soon as competent builders like Gavin Wooden and Jeffrey Wilcke, who didn’t share my deficiencies in potential to jot down p2p networking code, joined the challenge, and as soon as sufficient individuals have been excited that I noticed there can be cash to rent extra, I made the choice to instantly transfer to an unbiased blockchain. The reasoning for this selection I described in my whitepaper in early January:
The benefit of a metacoin protocol is that it could actually permit for extra superior transaction varieties, together with customized currencies, decentralized trade, derivatives, and many others, which can be not possible on high of Bitcoin itself. Nevertheless, metacoins on high of Bitcoin have one main flaw: simplified cost verification, already tough with coloured cash, is outright not possible on a metacoin. The reason being that whereas one can use SPV to find out that there’s a transaction sending 30 metacoins to handle X, that by itself doesn’t imply that handle X has 30 metacoins; what if the sender of the transaction didn’t have 30 metacoins to begin with and so the transaction is invalid? Discovering out any half of the present state basically requires scanning by way of all transactions going again to the metacoin’s authentic launch to determine which transactions are legitimate and which of them will not be. This makes it not possible to have a really safe consumer with out downloading the complete 12 GB Bitcoin blockchain.
Primarily, metacoins do not work for mild shoppers, making them relatively insecure for smartphones, customers with outdated computer systems, internet-of-things units, and as soon as the blockchain scales sufficient for desktop customers as nicely. Ethereum’s unbiased blockchain, however, is particularly designed with a extremely superior mild consumer protocol; in contrast to with meta-protocols, contracts on high of Ethereum inherit the Ethereum blockchain’s mild client-friendliness properties absolutely. Lastly, lengthy after that, I noticed that by making an unbiased blockchain permits us to experiment with stronger variations of GHOST-style protocols, safely pulling down the block time to 12 seconds.
So what is the level of this story? Primarily, had historical past been totally different, we simply might have gone the route of being “on high of Bitcoin” proper from day one (in actual fact, we nonetheless might make that pivot if desired), however strong technical causes existed then why we deemed it higher to construct an unbiased blockchain, and these causes nonetheless exist, in just about precisely the identical kind, at this time.
Since a variety of readers have been anticipating a response to how Ethereum as an unbiased blockchain can be helpful even within the face of the latest announcement of a metacoin based mostly on Ethereum expertise, that is it. Scalability. Should you use a metacoin on BTC, you achieve the good thing about having simpler back-and-forth interplay with the Bitcoin blockchain, however if you happen to create an unbiased chain then you’ve the power to realize a lot stronger ensures of safety notably for weak units. There are actually purposes for which the next diploma of connectivity with BTC is vital ; for these circumstances a metacoin will surely be superior (though observe that even an unbiased blockchain can work together with BTC fairly nicely utilizing mainly the identical expertise that we’ll describe in the remainder of this weblog submit). Thus, on the entire, it would actually assist the ecosystem if the identical standardized EVM is obtainable throughout all platforms.
Past 1.0
Nevertheless, in the long run, even mild shoppers are an unpleasant resolution. If we really anticipate cryptoeconomic platforms to grow to be a base layer for a really great amount of world infrastructure, then there might nicely find yourself being so many crypto-transactions altogether that no laptop, besides perhaps a couple of very massive server farms run by the likes of Google and Amazon, is highly effective sufficient to course of all of them. Thus, we have to break the basic barrier of cryptocurrency: that there have to exist nodes that course of each transaction. Breaking that barrier is what will get a cryptoeconomic platform’s database from being merely massively replicated to being really distributed. Nevertheless, breaking the barrier is tough, notably if you happen to nonetheless wish to preserve the requirement that all the totally different elements of the ecosystem ought to reinforce one another’s safety.
To attain the purpose, there are three main methods:
- Constructing protocols on high of Ethereum that use Ethereum solely as an auditing-backend-of-last-resort, conserving transaction charges.
- Turning the blockchain into one thing a lot nearer to a high-dimensional interlinking mesh with all elements of the database reinforcing one another over time.
- Going again to a mannequin of one-protocol (or one service)-per-chain, and developing with mechanisms for the chains to (1) work together, and (2) share consensus power.
Of those methods, observe that solely (1) is finally suitable with retaining the blockchain in a kind something near what the Bitcoin and Ethereum protocols help at this time. (2) requires an enormous redesign of the basic infrastructure, and (3) requires the creation of 1000’s of chains, and for fragility mitigation functions the optimum method can be to make use of 1000’s of currencies (to cut back the complexity on the person facet, we will use stable-coins to basically create a standard cross-chain forex commonplace, and any slight swings within the stable-coins on the person facet can be interpreted within the UI as curiosity or demurrage so the person solely must hold monitor of 1 unit of account).
We already mentioned (1) and (2) in earlier weblog posts, and so at this time we are going to present an introduction to a few of the ideas concerned in (3).
Multichain
The mannequin right here is in some ways just like the Bitshares mannequin, besides that we don’t assume that DPOS (or some other POS) can be safe for arbitrarily small chains. Fairly, seeing the final sturdy parallels between cryptoeconomics and establishments in wider society, notably authorized methods, we observe that there exists a big physique of shareholder regulation defending minority stakeholders in real-world corporations towards the equal of a 51% assault (particularly, 51% of shareholders voting to pay 100% of funds to themselves), and so we attempt to replicate the identical system right here by having each chain, to a point, “police” each different chain both instantly or not directly by way of an interlinking transitive graph. The form of policing required is easy – policing aganist double-spends and censorship assaults from native majority coalitions, and so the related guard mechanisms will be carried out fully in code.
Nevertheless, earlier than we get to the exhausting downside of inter-chain safety, allow us to first focus on what truly seems to be a a lot simpler downside: inter-chain interplay. What can we imply by a number of chains “interacting”? Formally, the phrase can imply considered one of two issues:
- Inside entities (ie. scripts, contracts) in chain A are capable of securely be taught info concerning the state of chain B (data switch)
- It’s attainable to create a pair of transactions, T in A and T’ in B, such that both each T and T’ get confirmed or neither do (atomic transactions)
A sufficiently normal implementation of (1) implies (2), since “T’ was (or was not) confirmed in B” is a reality concerning the state of chain B. The best means to do that is by way of Merkle bushes, described in additional element right here and right here; basically Merkle bushes permit the complete state of a blockchain to be hashed into the block header in such a means that one can give you a “proof” {that a} explicit worth is at a selected place within the tree that’s solely logarithmic in dimension in the complete state (ie. at most a couple of kilobytes lengthy). The final thought is that contracts in a single chain validate these Merkle tree proofs of contracts within the different chain.
A problem that’s higher for some consensus algorithms than others is, how does the contract in a sequence validate the precise blocks in one other chain? Primarily, what you find yourself having is a contract performing as a fully-fledged “mild consumer” for the opposite chain, processing blocks in that chain and probabilistically verifying transactions (and retaining monitor of challenges) to make sure safety. For this mechanism to be viable, at the very least some amount of proof of labor should exist on every block, in order that it isn’t attainable to cheaply produce many blocks for which it’s exhausting to find out that they’re invalid; as a normal rule, the work required by the blockmaker to supply a block ought to exceed the price to the complete community mixed of rejecting it.
Moreover, we must always observe that contracts are silly; they aren’t able to taking a look at repute, social consensus or some other such “fuzzy” metrics of whether or not or not a given blockchain is legitimate; therefore, purely “subjective” Ripple-style consensus can be tough to make work in a multi-chain setting. Bitcoin’s proof of labor is (absolutely in concept, largely in observe) “goal”: there’s a exact definition of what the present state is (particularly, the state reached by processing the chain with the longest proof of labor), and any node on the planet, seeing the gathering of all out there blocks, will come to the identical conclusion on which chain (and subsequently which state) is appropriate. Proof-of-stake methods, opposite to what many cryptocurrency builders suppose, will be safe, however must be “weakly subjective” – that’s, nodes that have been on-line at the very least as soon as each N days because the chain’s inception will essentially converge on the identical conclusion, however long-dormant nodes and new nodes want a hash as an preliminary pointer. That is wanted to stop sure lessons of unavoidable long-range assaults. Weakly subjective consensus works positive with contracts-as-automated-light-clients, since contracts are at all times “on-line”.
Notice that it’s attainable to help atomic transactions with out data switch; TierNolan’s secret revelation protocol can be utilized to do that even between comparatively dumb chains like BTC and DOGE. Therefore, basically interplay isn’t too tough.
Safety
The bigger downside, nonetheless, is safety. Blockchains are weak to 51% assaults, and smaller blockchains are weak to smaller 51% assaults. Ideally, if we wish safety, we wish for a number of chains to have the ability to piggyback on one another’s safety, in order that no chain will be attacked except each chain is attacked on the identical time. Inside this framework, there are two main paradigm decisions that we will make: centralized or decentralized.
| Centralized | Decentralized |
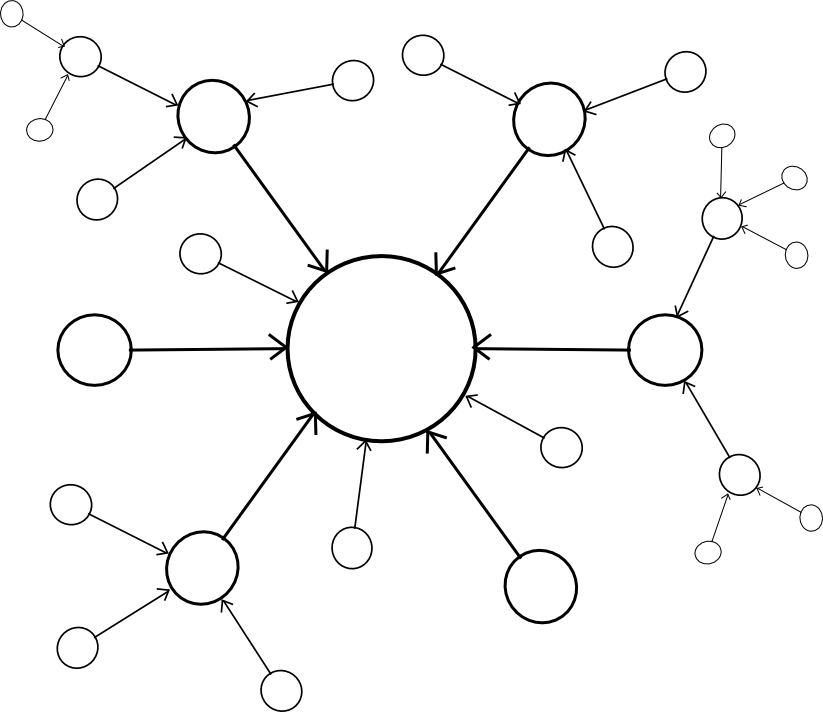 |
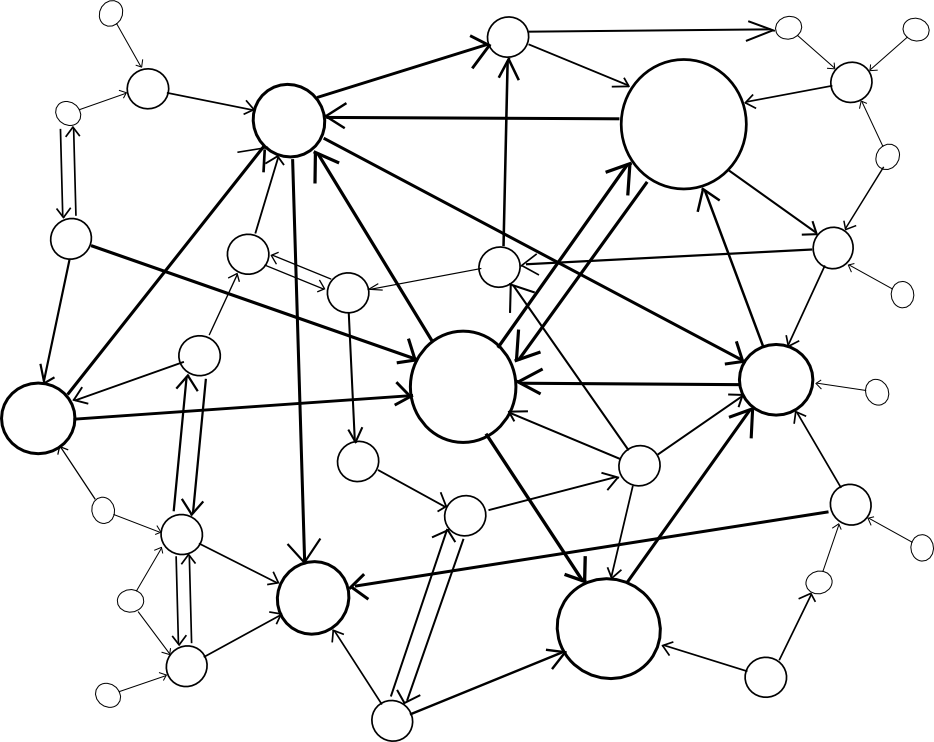 |
A centralized paradigm is basically each chain, whether or not instantly or not directly, piggybacking off of a single grasp chain; Bitcoin proponents typically like to see the central chain being Bitcoin, although sadly it might be one thing else since Bitcoin was not precisely designed with the required degree of general-purpose performance in thoughts. A decentralized paradigm is one that appears vaguely like Ripple’s community of distinctive node lists, besides working throughout chains: each chain has an inventory of different consensus mechanisms that it trusts, and people mechanisms collectively decide block validity.
The centralized paradigm has the profit that it is less complicated; the decentralized paradigm has the profit that it permits for a cryptoeconomy to extra simply swap out totally different items for one another, so it doesn’t find yourself resting on a long time of outdated protocols. Nevertheless, the query is, how can we truly “piggyback” on a number of different chains’ safety?
To offer a solution to this query, we’ll first give you a formalism known as an assisted scoring operate. Generally, the way in which blockchains work is that they have some scoring operate for blocks, and the top-scoring block turns into the block defining the present state. Assisted scoring features work by scoring blocks based mostly on not simply the blocks themselves, but in addition checkpoints in another chain (or a number of chains). The final precept is that we use the checkpoints to find out {that a} given fork, despite the fact that it might look like dominant from the perspective of the native chain, will be decided to have come later by way of the checkpointing course of.
A easy method is {that a} node penalizes forks the place the blocks are too far aside from one another in time, the place the time of a block is decided by the median of the earliest recognized checkpoint of that block within the different chains; this may detect and penalize forks that occur after the very fact. Nevertheless, there are two issues with this method:
- An attacker can submit the hashes of the blocks into the checkpoint chains on time, after which solely reveal the blocks later
- An attacker might merely let two forks of a blockchain develop roughly evenly concurrently, after which ultimately push on his most well-liked fork with full drive
To take care of (2), we will say that solely the legitimate block of a given block quantity with the earliest common checkpointing time will be a part of the principle chain, thus basically utterly stopping double-spends and even censorship forks; each new block would have to level to the final recognized earlier block. Nevertheless, this does nothing towards (1). To unravel (1), one of the best normal options contain some idea of “voting on information availability” (see additionally: Jasper den Ouden’s earlier submit speaking a couple of related thought); basically, the contributors within the checkpointing contract on every of the opposite chains would Schelling-vote on whether or not or not the complete information of the block was out there on the time the checkpoint was made, and a checkpoint can be rejected if the vote leans towards “no”.
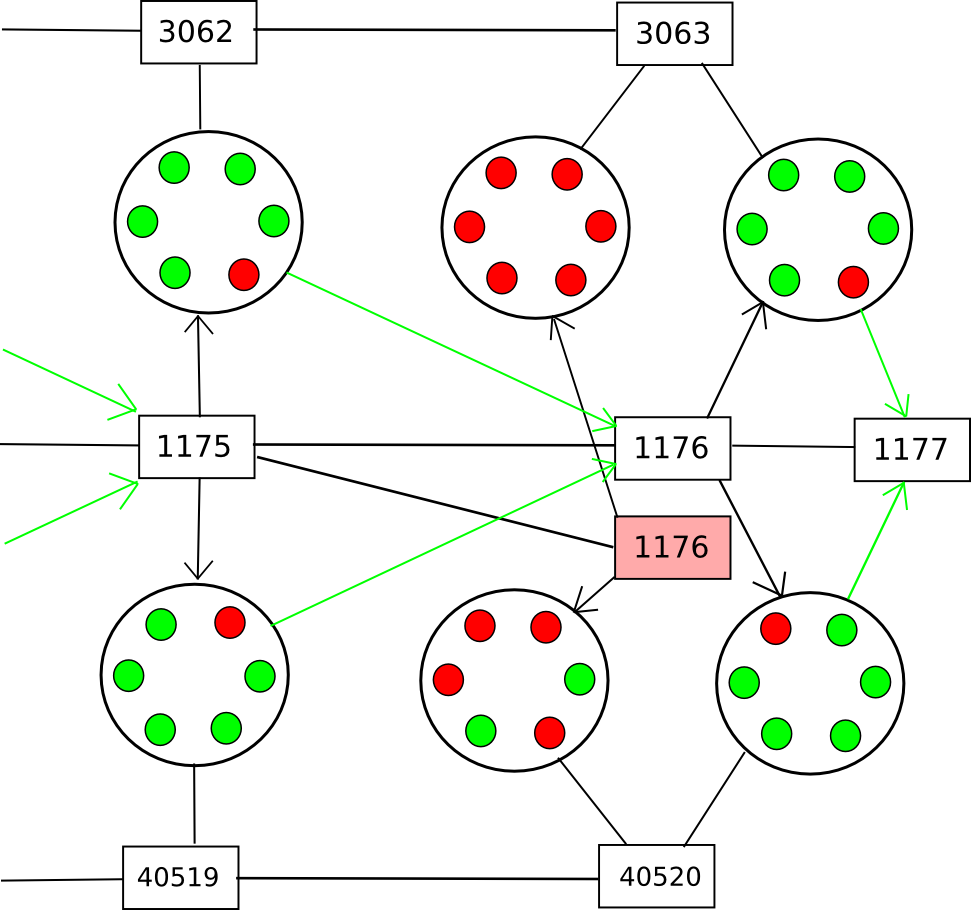
Notice that there are two variations of this technique. The primary is a technique the place contributors vote on information availability solely (ie. that each a part of the block is on the market on-line). This permits the voters to be relatively silly, and be capable to vote on availability for any blockchain; the method for figuring out information availability merely consists of repeatedly doing a reverse hash lookup question on the community till all of the “leaf nodes” are discovered and ensuring that nothing is lacking. A intelligent technique to drive nodes to not be lazy when doing this test is to ask them to recompute and vote on the foundation hash of the block utilizing a unique hash operate. As soon as all the info is obtainable, if the block is invalid an environment friendly Merkle-tree proof of invalidity will be submitted to the contract (or just revealed and left for nodes to obtain when figuring out whether or not or to not depend the given checkpoint).
The second technique is much less modular: have the Schelling-vote contributors vote on block validity. This is able to make the method considerably less complicated, however at the price of making it extra chain-specific: you would want to have the supply code for a given blockchain so as to have the ability to vote on it. Thus, you’ll get fewer voters offering safety on your chain mechanically. No matter which of those two methods is used, the chain might subsidize the Schelling-vote contract on the opposite chain(s) by way of a cross-chain trade.
The Scalability Half
Up till now, we nonetheless haven’t any precise “scalability”; a sequence is simply as safe because the variety of nodes which can be prepared to obtain (though not course of) each block. After all, there are answers to this downside: challenge-response protocols and randomly chosen juries, each described in the earlier weblog submit on hypercubes, are the 2 which can be presently best-known. Nevertheless, the answer right here is considerably totally different: as a substitute of setting in stone and institutionalizing one explicit algorithm, we’re merely going to let the market resolve.
The “market” is outlined as follows:
- Chains wish to be safe, and wish to save on assets. Chains want to pick out a number of Schelling-vote contracts (or different mechanisms probably) to function sources of safety (demand)
- Schelling-vote contracts function sources of safety (provide). Schelling-vote contracts differ on how a lot they must be backed to be able to safe a given degree of participation (value) and the way tough it’s for an attacker to bribe or take over the schelling-vote to drive it to ship an incorrect outcome (high quality).
Therefore, the cryptoeconomy will naturally gravitate towards schelling-vote contracts that present higher safety at a lower cost, and the customers of these contracts will profit from being afforded extra voting alternatives. Nevertheless, merely saying that an incentive exists isn’t sufficient; a relatively massive incentive exists to treatment getting older and we’re nonetheless fairly removed from that. We additionally want to point out that scalability is definitely attainable.
The higher of the 2 algorithms described within the submit on hypercubes, jury choice, is easy. For each block, a random 200 nodes are chosen to vote on it. The set of 200 is sort of as safe as the complete set of voters, because the particular 200 will not be picked forward of time and an attacker would want to regulate over 40% of the contributors to be able to have any important likelihood of getting 50% of any set of 200. If we’re separating voting on information availability from voting on validity, then these 200 will be chosen from the set of all contributors in a single summary Schelling-voting contract on the chain, because it’s attainable to vote on the info availability of a block with out truly understanding something concerning the blockchain’s guidelines. Thus, as a substitute of each node within the community validating the block, solely 200 validate the info, after which just a few nodes have to search for precise errors, since if even one node finds an error will probably be capable of assemble a proof and warn everybody else.
Conclusion
So, what’s the finish results of all this? Primarily, now we have 1000’s of chains, some with one utility, but in addition with general-purpose chains like Ethereum as a result of some purposes profit from the extraordinarily tight interoperability that being inside a single digital machine affords. Every chain would outsource the important thing a part of consensus to a number of voting mechanisms on different chains, and these mechanisms can be organized in numerous methods to verify they’re as incorruptible as attainable. As a result of safety will be taken from all chains, a big portion of the stake in the complete cryptoeconomy can be used to guard each chain.
It might show essential to sacrifice safety to some extent; if an attacker has 26% of the stake then the attacker can do a 51% takeover of 51% of the subcontracted voting mechanisms or Schelling-pools on the market; nonetheless, 26% of stake remains to be a big safety margin to have in a hypothetical multi-trillion-dollar cryptoeconomy, and so the tradeoff could also be value it.
The true advantage of this sort of scheme is simply how little must be standardized. Every chain, upon creation, can select some variety of Schelling-voting swimming pools to belief and subsidize for safety, and by way of a custom-made contract it could actually alter to any interface. Merkle bushes will must be suitable with all the totally different voting swimming pools, however the one factor that must be standardized there’s the hash algorithm. Totally different chains can use totally different currencies, utilizing stable-coins to offer a fairly constant cross-chain unit of worth (and, in fact, these stable-coins can themselves work together with different chains that implement numerous sorts of endogenous and exogenous estimators). Finally, the imaginative and prescient of considered one of 1000’s of chains, with the totally different chains “shopping for providers” from one another. Providers would possibly embrace information availability checking, timestamping, normal data provision (eg. value feeds, estimators), non-public information storage (probably even consensus on non-public information by way of secret sharing), and way more. The last word distributed crypto-economy.
from Ethereum – My Blog https://ift.tt/1bFh5mt
via IFTTT
No comments:
Post a Comment